Continued from Volume 42, Number 2. The final piece in this series is Volume 43, Number 1.
In our previous article, we explored operational aspects of cybersecurity. This one focuses on data governance and discusses how it permeates all operations and what can be done to strengthen it.
Recent research from the McKinsey Global Institute (MGI) published in a Harvard Business Review study1 remarks that the real estate industry does not rank well in its Digitization Index. According to MGI, while real estate is doing better on digital spending per worker and for transactions, there is a huge room for improvement in advancing the digitization of physical assets. This underscores the urgency (and opportunity) to address data and consider it an asset. In our industry, like all others, data management is evolving and data governance has become a critical issue to achieve competitive advantage.
In this article we explore:
- What is Data Governance?
- Are you treating data as a corporate resource?
- How are you handling and protecting the data?
What is Data Governance?
Data Governance (DG) are the policies that define the overall management of the availability, usability, integrity, and security of data used in an enterprise. A sound DG program includes a governing body, a defined set of procedures, and a clear plan to execute those procedures.2
The initial step in implementing a DG framework involves defining the owners and custodians of the data assets in the enterprise. Processes must then be defined to effectively cover how the data will be stored, archived, backed up, and protected from mishaps, theft, or attacks. A set of standards and procedures must be developed to define how the data is to be used by authorized personnel. Finally, a set of controls and audit procedures must be put into place that ensures ongoing compliance with internal data policies and external government regulations, and guarantees data is used in a consistent manner across multiple enterprise applications.
The diagram below provides an example of Data Governance foundations.
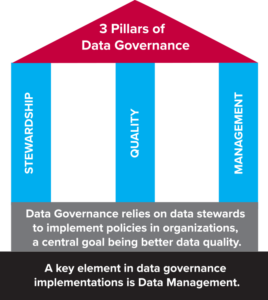
Are You Treating the Data as a Corporate Resource?
Data must also be recognized as a corporate resource. Everyone in an organization – and everyone the organization comes into contact with – has a role in the creation, maintenance, storage, and protection of data.
But how, then, do we define the right data? The right data are the details needed by the information system to enhance the performance of the company or the project. For Data Governance to be effective, we must collect, analyze, and protect the right data. The problem today is that because it is so easy to collect data, organizations are drowning in data, which makes effective governance and data analysis almost impossible. In fact, too much data may even obscure transparency. For example, the French regulator (AMF, “Autorité des Marchés Financiers”) sees too much data submission as a red flag for risk. Another frequent example comes from appraisals following mindless Real Estate templates and presenting endless data without thoughtful analysis.
By defining what constitutes “right data,” an organization can become more selective about data, resulting in more efficient and cost-effective databases and analytics – and so generating the right information. This approach not only reduces costs and speeds-up response times but also requires us to better understand the data needs of our consulting engagements and business. So, eventually, the question really is not “Do we store it?” but “What do we store?” Right data is the data that contains the information needed to help the organization reliably achieve its strategic goals.3 This consideration also becomes essential when designing disaster recovery and business continuity plans.
Where should Data Governance be located?
Typically, data management has been the purview of IT specialists, and has meant data capture and storage in data warehouses, and data mapping and various interfaces re-wiring. Routinely, data scrubbing has been equated to data quality efforts.
Since Data Governance is much more comprehensive than data management, it follows that it should be handled differently. If IT departments, senior business management, and boards of directors should be concerned and proactive about cybersecurity, then as with all risks, the responsibility for cybersecurity ultimately lies with everyone. Once Data Governance has been established, and policies put in place, it becomes everyone’s stewardship.
According to Fortune Magazine the question of who owns the data is about to get a lot more complicated.4 Business owners and executives need to pay close attention to what data their companies are sharing, with whom, and whether their technology providers will claim ownership of that information. That data has value, not only to the company generating it, but to the technology companies that provide the data-crunching services. And as the whole notion of “big data” involves aggregating data from many sources, analyzing it, and slicing and dicing it, the issue of data origin and ownership becomes more challenging than ever before.
“The value chain of who owns the data is complicated already and as you aggregate more sources it just gets more complicated,” said Dan Vesset, IDC’s Group VP for Analytics and Information Management. Consider companies such as Dropbox and SalesForce.com. These and other cloud-based applications are used routinely by real estate companies, yet how many Data Governance policies include 3rd-party apps in their evaluation and risk management?
Who should be educated on Data Governance?
Training is necessary to ensure that employees fully understand what is required of them. This is particularly important for those who have no previous knowledge or exposure to DG and why it may benefit them. DG initiatives should be targeted at increasing visibility of data across the enterprise, offering improved visibility to internal and external customers as well as compliance with regulations. DG provides a framework to move data up the value chain from data to information to knowledge. Knowledge is power, and people react best to a change in work practice when it is clearly articulated. Educating the workforce on the DG program is a key to acceptance and sustainability.
How are You Handling the Data?
If the well heralded scandals of Equifax, Yahoo, Facebook had not given data users and collectors much pause as to what happens to their data upstream and downstream, the recent GDPR (General Data Protection Regulation) and all updates to privacy notices it generated was a stark reminder that more control was needed. If compliance has been structured in various degrees of completeness and transparencies, it is still a much-welcomed progress.
Life Cycle of Data: Creation, Managing, Updating, Sharing, Deletion…
Whether data is primary or secondary, quality is a must in terms of timeliness, accuracy, and relevance. Good data comes at a cost not only directly through acquisition or subscription to data bases, or indirectly through staff time spent collecting and manipulating it before it becomes knowledge and a decision-making tool. Costs can be high to recreate or regain access to data lost to inadequate back-ups or inadvertent corruption or deletion. As for costs of bad data leading to poor decisions, the sky is the limit!
As any asset or resource, data must be protected, and its related budget considered a necessary investment in doing business and not a place to be thrifty.
The 4V’s of data first described by IBM – volume, velocity, variety and veracity – have since been expanded to 10.5 Of those additional “V features”, two are critical: validity – or relevance -, and value, as we discussed earlier, explaining the “right data” as corporate assets. Data life cycle should be of concern not only internally but externally.
Do we have a vetting process for when data comes in and when it leaves our control?
Organizing a data flow is necessary because it documents how the various business lines use the data: why is the data needed in the first place, how end-users process it, and what happens to this data from creating to storing to using to sharing to updating, and finally to archiving or deleting. Once no longer useful, is the data deleted or destroyed, and how is it destroyed? A defined data life cycle and workflow is essential to a DG policy.
The accelerated turnaround times and business requirements encourage sharing data and applications among the servers and networks of investors, owners, and tenants. Internet of Things (IoT), Shared Services, and control systems such as BIMs or simply HVAC, multiply the opportunities of data being compromised or stolen. The same data issues raised and resolved internally should be addressed for interactions with third parties.
Blockchain is the newest “solution” to data protection. However, it is important to remember that your data protection is only as strong as the weakest link in the process. People are trying to understand the distributed ledger concept but are having trouble getting their arms around the entire concept and its use in digital transactions. Who is taking control and how are you controlling the quality, performance, and reporting requirements when blockchain technology is utilized? Also, legal agreements among the various parties involved have yet to be understood and written to protect the premise on which Blockchain is being developed.
Another area to be aware of is GDPR6 and its effect on data management. The European Union’s General Data Protection Regulation went into effect on May 25, 2018. GDPR replaces the EU Data Protection Directive. GDPR may apply to US-based businesses even if they do not have offices or employees in the EU. It can also reach activities conducted outside the EU.
Does it take into account other parties connected to the data?
Here is a CRE engagement example and the critical role played by other parties in protecting or exposing sensitive data. The loop diagram below shows the relationship of the various parties to the process. As you can see from the example and the loop diagram, each of the parties is connected to the other parties. Therefore, the focus must be on the identification of vulnerabilities in the system – as multiple systems are interacting variously – in order to adequately protect the data. Remember, a breach in one is a breach in all.
CRE Engagement Example
A CRE has been engaged for the following advice: The client, a large investor owns its building, occupies a couple of floors but needs to expand and does not know which way to go:
- Stay put, rationalize their space since they cannot expand in their own building which is fully occupied
- Sell the existing building, buy a much larger one they have been interested in and take several floors since it has a few vacancies
- Stay put and buy
Here is (part of) the information collection process:
- Sign the NDA and collect internal information
- their staff and operations
- their business plan and strategy,
- need contact with HR, business lines, legal department
- client sends info and you open the documents while in the airport lounge, and continue working on them on the plane
- Collect info on building for sale:
- sign other NDA
- contact the broker, the title company, the tax office, the planning department….
- obtain operating expenses
- obtain rent roll
- obtain appraisal report
- obtain engineering and environmental reports
- you work on those documents from your hotel room, on free WIFI
- Send leases for abstraction in India
- Share CRE report with executive committee members who open it while they are on the Eurostar
- Shop for best financing, approach several banks and send them an “information” package
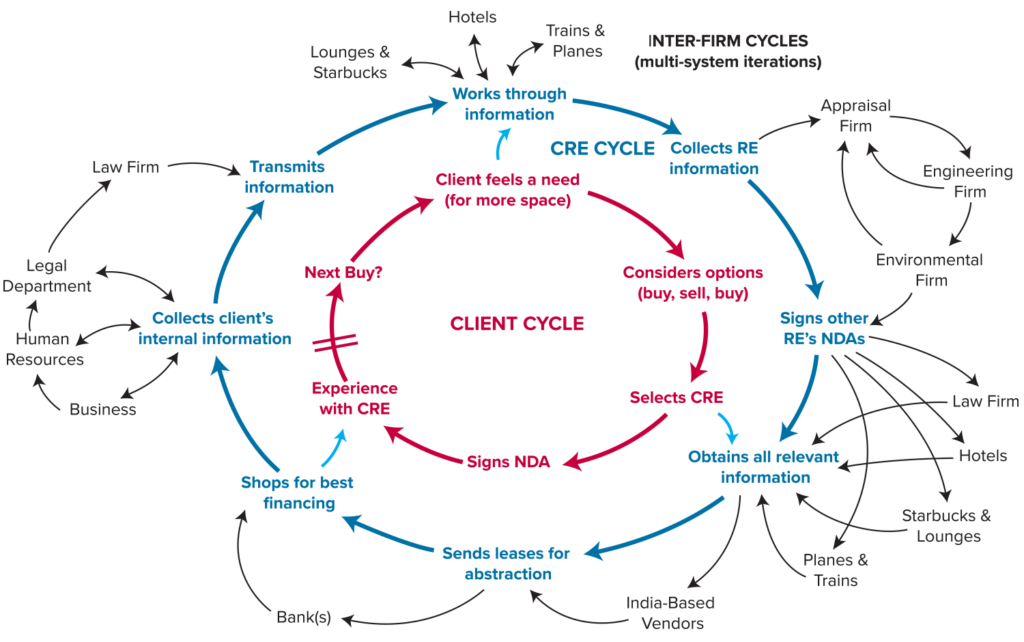
Source: Usman A. Ghani, Conflucore, llp. ©2018 All rights reserved.
Conclusion
In our industry as in all others, quantitative and qualitative data management has become a critical issue for remaining competitive. Real estate companies need to become more data-centric in their projects and activities. Robust policies for Data Governance will go far in mitigating cyber risks and be indispensable as our industry adopts innovative technologies like blockchain.
In a future article we will look at where the commercial real estate industry is heading given the rapid and disruptive changes brought about by smart technology, including smart cities, smart buildings, and the cyber issues surrounding Building Information Management (BIM).
Endnotes
1. Prashant Gandhi, Somesh Khanna, and Sree Ramaswamy, “Which industries are the most digital and why”, Harvard Business Review, 4/1/2016. ↩
2. http://searchdatamanagement.techtarget.com/definition/data-governance ↩
3. Savoie, Michael J. 2016. Building Successful Information Systems: Five Best Practices to Ensure Organizational Effectiveness and Profitability. Second Edition. ↩
4. http://fortune.com/2016/04/06/who-owns-the-data/ ↩
5. The Ten V’s of Big Data. George Firican. Upside, 02/08/2017. https://tdwi.org/articles/2017/02/08/10-vs-of-big-data.aspx ↩
6. GDPR impacts all companies doing business in the EU or with EU citizens around the world. That law lets users gain access to, and correct data that firms hold. It gives them the right to transfer their data out; and it requires companies to explain how they keep data secure. ↩


 Photo: Joyseulay/Shutterstock.com
Photo: Joyseulay/Shutterstock.com



